Tftp Server
Built-in File Transfer Capability. SecureCRT is one of the only terminal emulation clients available with a built-in TFTP server. This basic protocol allows a local system to send and receive binary files without the need to launch a separate application. However, you may also transfer files using other supported protocols, including: SFTP. Mar 26, 2020 As its name indicates, TFTP is a client/server for TFTP networks protocols and only a server for DHCP, SNTP y Syslog. TFTP protocol is a simpler version of the classic FTP which is used mainly to update the firmware on network devices such as routers, commuters or IP phones.
Trivial File Transfer Protocol (TFTP) is a simple lockstepFile Transfer Protocol which allows a client to get a file from or put a file onto a remote host. One of its primary uses is in the early stages of nodes booting from a local area network. TFTP has been used for this application because it is very simple to implement.
TFTP was first standardized in 1981[1] and the current specification for the protocol can be found in RFC 1350.
Overview[edit]
Due to its simple design, TFTP can be easily implemented by code with a small memory footprint. It is therefore the protocol of choice for the initial stages of any network booting strategy like BOOTP, PXE, BSDP, etc., when targeting from highly resourced computers to very low resourced Single-board computers (SBC) and System on a Chip (SoC). It is also used to transfer firmware images and configuration files to network appliances like routers, firewalls, IP phones, etc. Today, TFTP is virtually unused for Internet transfers.
TFTP's design was influenced from the earlier protocol EFTP, which was part of the PUPprotocol suite. TFTP was first defined in 1980 by IEN 133.[2]In June 1981 The TFTP Protocol (Revision 2) was published as RFC 783 and later updated in July 1992 by RFC 1350 which fixed among other things the Sorcerer's Apprentice Syndrome. In March 1995 the TFTP Option Extension RFC 1782 updated later in May 1998 by RFC 2347, defined the option negotiation mechanism which establishes the framework for file transfer options to be negotiated prior to the transfer using a mechanism which is consistent with TFTP's original specification.
TFTP is a simple protocol for transferring files, implemented on top of the UDP/IP protocols using well-known port number 69. TFTP was designed to be small and easy to implement, and therefore it lacks most of the advanced features offered by more robust file transfer protocols. TFTP only reads and writes files from or to a remote server. It cannot list, delete, or rename files or directories and it has no provisions for user authentication.Today TFTP is generally only used on local area networks (LAN).
Details[edit]
In TFTP, a transfer is initiated by the client issuing a request to read or write a particular file on the server. The request can optionally include a set of negotiated transfer parameters proposed by the client under the terms specified by RFC 2347. If the server grants the request, the file is sent in fixed length blocks of 512 bytes by default or the number specified in the blocksize negotiated option defined by RFC 2348. Each block of transferred data, which is usually carried within a single IP packet in order to avoid IP fragmentation, must be acknowledged by an acknowledgment packet before the next block can be sent. A data packet of less than 512 bytes or the agreed blocksize option signals termination of a transfer. If a packet gets lost in the network, the intended recipient will timeout and may retransmit their last packet (which may be data or an acknowledgment), thus causing the sender of the lost packet to retransmit that lost packet. The sender has to keep just one packet on hand for retransmission, since the lock step acknowledgment guarantees that all older packets have been correctly received. Notice that both devices involved in a transfer are considered senders and receivers. One sends data and receives acknowledgments, the other sends acknowledgments and receives data.
TFTP defines three modes of transfer: netascii, octet, and mail.
- Netascii is a modified form of ASCII, defined in RFC 764. It consists of an 8-bit extension of the 7-bit ASCII character space from 0x20 to 0x7F (the printable characters and the space) and eight of the control characters. The allowed control characters include the null (0x00), the line feed (LF, 0x0A), and the carriage return (CR, 0x0D). Netascii also requires that the end of line marker on a host be translated to the character pair CR LF for transmission, and that any CR must be followed by either a LF or the null.
- Octet allows for the transfer of arbitrary raw 8-bit bytes, with the received file resulting byte-per-byte identical to the one sent. More correctly, if a host receives an octet file and then returns it, the returned file must be identical to the original.[3]
- Mail transfer mode uses Netascii transfer, but the file is sent to an email recipient by specifying that recipient's email address as the file name. RFC 1350 declared this mode of transfer obsolete.
TFTP uses UDP as its transport protocol. A transfer request is always initiated targeting port 69, but the data transfer ports are chosen independently by the sender and receiver during the transfer initialization. The ports are chosen at random according to the parameters of the networking stack, typically from the range of ephemeral ports.[4]
- The initiating host A sends an RRQ (read request) or WRQ (write request) packet to host S at port number 69, containing the filename, transfer mode, and optionally any negotiated option under the terms of RFC 2347.
- S replies with an option ACK if options were used, and an ACK (acknowledgement) packet to WRQ and directly with a DATA packet to RRQ. Packet is sent from a randomly allocated ephemeral port, and all future packets to host S should be directed to this port.
- The source host sends numbered DATA packets to the destination host, all but the last containing a full-sized block of data (512 bytes default). The destination host replies with numbered ACK packets for all DATA packets.
- The final DATA packet must contain less than a full-sized block of data to signal that it is the last. If the size of the transferred file is an exact multiple of the block-size, the source sends a final DATA packet containing 0 bytes of data.
- Receiver responds to each DATA with associated numbered ACK. Sender responds to the first received ACK of a block with DATA of the next block.
- If an ACK is not eventually received, a retransmit timer re-sends DATA packet.
TFTP has always been associated to network booting. One of the first attempts in this regard was the Bootstrap Loading using TFTP standard RFC 906, published in 1984, which established the 1981 published Trivial File Transfer Protocol standard RFC 783 to be used as the standard file transfer protocol for bootstrap loading. It was followed shortly after by the Bootstrap Protocol standard RFC 951 (BOOTP), published in 1985, which allowed a disk-less client machine to discover its own IP address, the address of a TFTP server, and the name of a Network Bootstrap Program (NBP) to be TFTP transferred, loaded into memory, and executed. Dynamic Host Configuration Protocol standard RFC 2131 (DHCP) published in 1997 improved BOOTP capabilities. Finally, the Preboot Execution Environment (PXE) version 2.0 was released in December 1998, and the update 2.1 was made public in September 1999 counting on TFTP as its file transfer protocol.[5] Intel has recently decided to widely support PXE within the new UEFI specification extending the TFTP support to all EFI/UEFI environments.[6][7]
The original protocol has a transfer file size limit of 512 bytes/block x 65535 blocks = 32 MB. In 1998 this limit was extended to 65535 bytes/block x 65535 blocks = 4 GB by TFTP Blocksize Option RFC 2348. If the defined blocksize produces an IP packet size that exceeds the minimum MTU at any point of the network path, IP fragmentation and reassembly will occur not only adding more overhead[8] but also leading to total transfer failure when the minimalist IP stack implementation in a host's BOOTP or PXE ROM does not (or fails to properly) implement IP fragmentation and reassembly.[9] If TFTP packets should be kept within the standard Ethernet MTU (1500), the blocksize value is calculated as 1500 minus headers of TFTP (4 bytes), UDP (8 bytes) and IP (20 bytes) = 1468 bytes/block, this gives a limit of 1468 bytes/block x 65535 blocks = 92 MB. Today most servers and clients support block number roll-over (block counter going back to 0 or 1[10] after 65535) which gives an essentially unlimited transfer file size.
Since TFTP utilizes UDP, it has to supply its own transport and session support. Each file transferred via TFTP constitutes an independent exchange. Classically, this transfer is performed in lock-step, with only one packet (either a block of data, or an 'acknowledgement') alternatively in flight on the network at any time. Due to this single data block strategy instead of sending a larger amount of uninterrupted data blocks before pausing the transfer to wait for the corresponding acknowledge (windowing), TFTP provides low throughput especially over high latency links. Microsoft introduced windowed TFTP in Windows 2008 as part of their Windows Deployment Services (WDS), in January 2015 TFTP Windowsize Option RFC 7440 was published. This substantially improves performance for things like PXE booting without the IP fragmentation side effect sometimes observed on Blocksize Option RFC 2348[11]
Security considerations[edit]
TFTP includes no login or access control mechanisms. Care must be taken when using TFTP for file transfers where authentication, access control, confidentiality, or integrity checking are needed. Note that those security services could be supplied above or below the layer at which TFTP runs. Care must also be taken in the rights granted to a TFTP server process so as not to violate the security of the server's file system. TFTP is often installed with controls such that only files that have public read access are available via TFTP. Also listing, deleting, renaming, and writing files via TFTP are typically disallowed. TFTP file transfers are not recommended where the inherent protocol limitations could raise insurmountable liability concerns.[12]
IETF standards documentation[edit]
| RFC Number | Title | Published | Author | Obsolete and Update Information |
|---|---|---|---|---|
| RFC 783 | The TFTP Protocol (Revision 1) | June 1981 | K. Sollins | Obsoleted by - RFC 1350 |
| RFC 906 | Bootstrap Loading using TFTP | June 1984 | Ross Finlayson | - |
| RFC 951 | Bootstrap Protocol | Sep.1985 | Bill Croft | Updated by RFC 1395, RFC 1497, RFC 1532, RFC 1542, RFC 5494 |
| RFC 1350 | The TFTP Protocol (Revision 2) | July 1992 | K. Sollins | Updated by RFC 1782, RFC 1783, RFC 1784, RFC 1785, RFC 2347, RFC 2348, RFC 2349 |
| RFC 1782 | TFTP Option Extension | March 1995 | G. Malkin | Obsoleted by - RFC 2347 |
| RFC 2131 | Dynamic Host Configuration Protocol | March 1997 | R. Droms | Updated by RFC 3396, RFC 4361, RFC 5494, RFC 6842 |
| RFC 2347 | TFTP Option Extension | May 1998 | G. Malkin | - |
| RFC 2348 | TFTP Blocksize Option | May 1998 | G. Malkin | - |
| RFC 2349 | TFTP Timeout Interval and Transfer Size Options | May 1998 | G. Malkin | - |
| RFC 5505 | Principles of Internet Host Configuration | May 2009 | B. Aboba | - |
| RFC 7440 | TFTP Windowsize Option | Jan 2015 | P. Masotta | - |
See also[edit]
References[edit]
Tftp Server Ubuntu
- ^RFC 783
- ^Karen R. Sollins (1980-01-29). The TFTP Protocol. IETF. IEN 133. Retrieved 2010-05-01.
- ^RFC 1350, page 5.
- ^Karen R.Sollins (July 1992). The TFTP Protocol (Revision 2). IETF. doi:10.17487/RFC1350. RFC1350. Retrieved 2010-05-01.
- ^'Preboot Execution Environment (PXE) Specification - Version 2.1'(PDF). Intel Corporation. 1999-09-20. Archived from the original(PDF) on 2013-11-02. Retrieved 2014-02-08.
- ^'Unified Extensible Firmware Interface Specification'(PDF). UEFI. 2013-12-02. Retrieved 2014-04-04.
- ^'UEFI PXE Boot Performance Analysis'(PDF). Intel Corporation. 2014-02-02. Archived from the original(PDF) on 2014-08-08. Retrieved 2014-04-04.
- ^RFC 2348, page 3.
- ^RFC 5505, page 7.
- ^'Extending TFTP'. CompuPhase. Retrieved 2018-12-12.
- ^RFC 7440, page 1.
- ^RFC 7440, page 7.
I first got acquainted with TFTP at the beginning of my networking career. The first use-case of TFTP protocol is when I first upgraded the IOS firmware of a Cisco router using a little software utility called “TFTPD32”.
Trivial File Transfer Protocol (TFTP) software provide a key service to many network and system administrators for routine software and firmware updates and transfers.
Devices that commonly work with TFTP servers for firmware and configuration transfers include network routers and switches, hardware firewalls, data streamers, VoIP phones, IT systems etc. It can also be helpful for managing large number of computer workstations.
TFTP is not a secure protocol designed to conduct file transfers over the Internet, however. For this kind of service, FTP and SFTP servers are a better choice.
Although it’s more commonly used for network administration in large intranets, TFTP is also useful in the home network setting. If you have a large file transfer you need to make between OSes that aren’t compatible, a TFTP server and client can be a solution for a quick-and-dirty setup.
There continues to be a number of free TFTP server options available for individuals and organizations to integrate into their systems. Below is a brief overview of nine TFTP server software that are free and open source in many cases.
Table of Contents
1. TFTPD32/64
TFTPD32 or TFTPD64 is the 32-bit or 64-bit Windows version of a French open source network utility package that includes a TFTP server. The services provided in addition to the TFTP server include DHCP, Syslog server, log viewer etc. A TFTP client is also in the package if you need one to install on network devices receiving files.
TFTPD32/64 is the brainchild of Phillipe Jounin, who has made it available to the public under the European Union Public License. It’s been implemented in projects like Cisco’s PIX and Aironet, HP’s Alpha servers, and Juniper’s Netscreen. It also won CNET’s Five Star Award in 2009 and is probably the oldest utility of its kind.
2. Solarwinds Free TFTP Server
Solarwinds offers a full suite of IT and network management software. Their free TFTP server is a stripped-down version of their Network Configuration Manager product, but it functions well for basic tasks like pushing out OS images to workstations or firmware to network devices periodically over an internal network.
It can handle files as large as 4 GB, concurrent transfers to many devices at once, and runs as a Windows service. It doesn’t have more advanced features like device backup and version control or change management tools, but it does manage which IP numbers are authorized for connections.
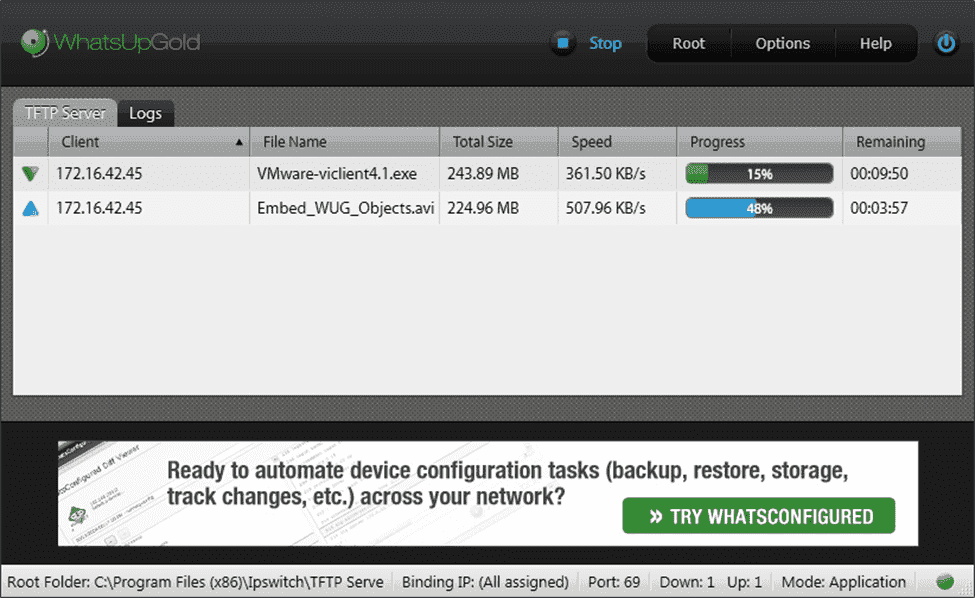
3. WhatsUp TFTP Server
Ipswitch is a software company that specializes in file transfer and network management tools. Their WhatsUp Gold TFTP Server is a free utility they offer for network engineers to add to their toolbox.
It allows automated file transfers to be set up for multiple computers and devices on an intranet with a dedicated schedule.
Whether you need a tool to reinstall a software configuration weekly or a way to push out firmware and application patches to dozens of devices, WhatsUp Gold can make your life easier.
Like other TFTP servers, it runs as an always-on service and can even schedule file transfers during low traffic hours.
4. WinAgents TFTP Server

WinAgents Software Group offers free downloads of their TFTP Server. It’s a legacy software designed to run on Windows 2000, 2003, Vista, and 7, which makes it useful if you work with these older OSes on your network. It can probably work with Windows 10 as well, you just need to try it.
WinAgents TFTP Server operates as a background service and implements an IP-based access control model for some kind of network security.
It also supports sending files through firewalls by configuring a UDP port for the connections. Administrators who manage large intranets or remote sites will find the remote configuration features helpful. The cache system makes the system highly scalable compared to other free TFTP tools.
5. haneWin TFTP Server
haneWin TFTP Server is a shareware offering for Windows. It supports both current and legacy Windows versions ranging from XP to Windows 10, and it can run as a service in the background on Windows 95/98/2000 without a user account logged in.
Data security options provided by haneWin include profiles based on the operation requested, IP address, and the file directories used by the server.
You can configure the server to transfer data through a range of UDP ports depending on your firewall settings and network traffic.
The client that comes with haneWin’s TFTP server is a Win32 console app that implements TFTP configurations in its command line options. For instance, you can set up a pipeline that will direct file transfers to other applications.
6. Open TFTP Server
Open TFTP Server is the work of Achal Dhir, who also offers freeware DHCP and DNS servers on SourceForge.
His TFTP Server is full-featured for basic file transfer automation, including multi-threaded operation for managing numerous connections at a time.
He provides support for most network configuration options like ports, block size, block number roll over, total size, and interval time settings.
It operates in the background as either a Unix daemon or a Windows service, and logging tools are included to help you monitor transfer activity.
7. Spiceworks TFTP Server
Spiceworks is a well-known networking and IT community with various relevant software tools as well.
One of their offerings include a network administration app that bundles a TFTP server for network configuration tasks.
The app includes an inventory tab that gives you a snapshot of all your network devices and workstations.
It includes an interface for scheduling file transfers like backups, configuration restore files, and firmware updates.
SpiceWorks also provides advanced features like comparing a device’s current software configuration with a backup to detect changes that have been made.
Whether you need to reset your workstations to a software configuration periodically or just want to schedule safe backups for repairing errors in the future, SpiceWorks can handle your TFTP server needs.
You will need to register and create an account in order to download.
8. Windows TFTP Utility
Windows TFTP Utility is another free server shared with the public on SourceForge. It supports a basic set of TFTP configuration options, including logging features. The developer also provides online instructions on how to integrate the server into other applications. It was built with Microsoft’s .NET platform.
Tftpd32 Server
9. TFTP Desktop
Free Tftp Server
Not all the TFTP servers are designed specifically for network administrators handling hundreds of workstations and routers on an intranet.
TFTP Desktop is a consumer app made for situations that can arise on home networks. It was released during the Windows 7 era and hasn’t received an update, so it’s limited to running on pre-Windows 8 computers.
It does, however, support Windows 98, so if you have a legacy computer you keep as a home server, this program can run on it. It’s a free trial download on CNET that’s fully functional, which makes it ideal for fixing temporary problems like transfering large files between incompatible OSes.
Comparison Between TFTP and FTP/SFTP
As I have mentioned at the beginning of this article, TFTP is not a secure protocol to use compared to FTP (File Transfer Protocol) or SFTP (Secure File Transfer Protocol) which uses SSH as underline protocol.
Tftp Server
Let’s see their main differences:
Solarwinds Tftp Server
| TFTP | FTP | SFTP |
| Uses Unreliable UDP communication | Uses Reliable TCP communication | Uses Reliable TCP communication |
| Works on UDP port 69 | Works on TCP port 20/21 | Works on TCP port 22 |
| Not Secure | Medium Security (using username/password) | Higher Security |
| No authentication | Uses username/password | Either username/password or SSH keys can be used |
| No encryption | No encryption | Traffic is Encrypted |